ASTM C1309-97(2003)
(Practice)Standard Practice for Performance Evaluation of In-Plant Walk-Through Metal Detectors
Standard Practice for Performance Evaluation of In-Plant Walk-Through Metal Detectors
SIGNIFICANCE AND USE
Walk-through metal detectors are an effective and unobtrusive means for searching for concealed metallic weapons and SNM (special nuclear material) shielding material. The detectors are generally applied to prevent the unauthorized entry of weapons into facilities, and theft or unauthorized removal of SNM. Daily functional testing of metal detectors shows that they are operating and will produce the correct alarm signal; the significant use of less frequent in-plant evaluations provides data from which to determine if detectors are operating at expected performance levels.
This practice provides a system of procedures for evaluating the detection performance of walk-through metal detectors.
The procedures specify data to be recorded and used for establishing, tracking, and auditing metal detector performance and operation.
This practice suggests documentation for maintaining performance records. Appendix X4 provides examples of forms for recording and tracking detector operation and performance testing.
SCOPE
1.1 This practice is one of several (see Appendix X1) developed to assist operators of nuclear facilities with meeting the metal detection performance requirements set by regulatory authorities.
1.2 This practice consists of four procedures useful for evaluating the in-plant performance of walk-through metal detectors (see Fig. 1).
1.2.1 Two of the procedures provide data for evaluating probability of detection. These procedures use binomial data (alarm/not alarm).
1.2.1.1 The detection sensitivity test (DST)² is the initial procedure in the detection probability evaluation series. It is used to establish the probability of detection immediately after the detector has been adjusted to its operational sensitivity setting.
1.2.1.2 The detection sensitivity verification test (DSVT)² procedure periodically provides data for evaluation of continuing detection performance.
1.2.2 The third procedure is a "functional test." It is used routinely to verify that a metal detector is operating and responds with the correct audio and visual signals when subjected to a condition that should cause an alarm.
1.2.3 The fourth procedure is used to verify that alarms generated during detection sensitivity testing were likely the result of the detection of metal and not caused by outside interferences or the perturbation of the detection field by the tester's body mass.
1.2.3.1 This procedure also can be used to establish a probability of occurrence for false alarms, for example, 20 test passes by a clean-tester resulting in no alarms indicates a false alarm probability of less than 0.15 at 95 % confidence. This procedure is optional unless required by the regulatory authority.
1.3 This practice does not set test object specifications. The specifications should be issued by the regulatory authority.
1.4 This practice is intended neither to set performance levels nor to limit or constrain technologies.
1.5 This practice does not address safety or operational issues associated with the use of walk-through metal detectors.
General Information
Relations
Standards Content (Sample)
NOTICE: This standard has either been superseded and replaced by a new version or withdrawn.
Contact ASTM International (www.astm.org) for the latest information
Designation: C1309 – 97 (Reapproved 2003)
Standard Practice for
Performance Evaluation of In-Plant Walk-Through Metal
1
Detectors
This standard is issued under the fixed designation C1309; the number immediately following the designation indicates the year of
original adoption or, in the case of revision, the year of last revision. A number in parentheses indicates the year of last reapproval. A
superscript epsilon (´) indicates an editorial change since the last revision or reapproval.
INTRODUCTION
Nuclear regulatory authorities require personnel entering designated security areas to be screened
for concealed weapons and personnel exiting areas containing specified quantities of special nuclear
material to be screened for metallic nuclear shielding materials. Portal-type walk-through metal
detectors are widely used to implement these requirements. This practice provides guidelines for
evaluating the in-plant performance of walk-through metal detectors.
1. Scope 1.2.3 The fourth procedure is used to verify that alarms
generated during detection sensitivity testing were likely the
1.1 This practice is one of several (see Appendix X1)
result of the detection of metal and not caused by outside
developed to assist operators of nuclear facilities with meeting
interferences or the perturbation of the detection field by the
themetaldetectionperformancerequirementssetbyregulatory
tester’s body mass.
authorities.
1.2.3.1 This procedure also can be used to establish a
1.2 This practice consists of four procedures useful for
probability of occurrence for false alarms, for example, 20 test
evaluating the in-plant performance of walk-through metal
passes by a clean-tester resulting in no alarms indicates a false
detectors (see Fig. 1).
alarm probability of less than 0.15 at 95 % confidence. This
1.2.1 Two of the procedures provide data for evaluating
procedure is optional unless required by the regulatory author-
probability of detection. These procedures use binomial data
ity.
(alarm/not alarm).
2 1.3 This practice does not set test object specifications. The
1.2.1.1 The detection sensitivity test (DST) is the initial
specifications should be issued by the regulatory authority.
procedure in the detection probability evaluation series. It is
1.4 This practice is intended neither to set performance
used to establish the probability of detection immediately after
levels nor to limit or constrain technologies.
the detector has been adjusted to its operational sensitivity
1.5 This practice does not address safety or operational
setting.
2
issues associated with the use of walk-through metal detectors.
1.2.1.2 The detection sensitivity verification test (DSVT)
procedure periodically provides data for evaluation of continu-
2. Referenced Documents
ing detection performance.
3
2.1 ASTM Standards:
1.2.2 The third procedure is a “functional test.” It is used
C1238 Guide for Installation of Walk-Through Metal De-
routinely to verify that a metal detector is operating and
tectors
responds with the correct audio and visual signals when
C1269 Practice for Adjusting the Operational Sensitivity
subjected to a condition that should cause an alarm.
Setting of In-Plant Walk-Through Metal Detectors
C1270 Practice for Detection Sensitivity Mapping of In-
1
This practice is under the jurisdiction of ASTM Committee C26 on Nuclear Plant Walk-Through Metal Detectors
Fuel Cycle and is the direct responsibility of Subcommittee C26.12 on Safeguard
F1468 Practice for Evaluation of Metallic Weapons Detec-
Applications.
tors for Controlled Access Search and Screening
Current edition approved Feb. 10, 2003. Published February 2003. Originally
approved in 1995. Last previous edition approved in 1997 as C1309 – 97. DOI:
10.1520/C1309-97R03.
2
The DST is one of two procedures used to evaluate detection rate. The
3
Detection Sensitivity Verification Test (DSVT) is the other. In the evaluation test For referenced ASTM standards, visit the ASTM website, www.astm.org, or
strategy, the DST is used to initially determine and document the detection rate and
contact ASTM Customer Service at service@astm.org. For Annual Book of ASTM
thentheDSVTisusedtoperiodicallycheckthatthedetectionratecontinuestomeet
Standards volume information, refer to the standard’s Document Summary page on
the requirements.
the ASTM website.
Copyright © ASTM International, 100 Barr Harbor Drive, PO Box C700, West Conshohocken, PA 19428-2959, United States.
1
---------------------- Page: 1 ----------------------
C1309 – 97 (2003)
NOTE 1—The number of detection sensitivity verification tests in a series, the number of passes per test, the acceptance criteria, and the frequency may
be established by regulatory authority or set by the security organization based on threat scenarios or vulnerability assessments; the numbers should be
suf
...







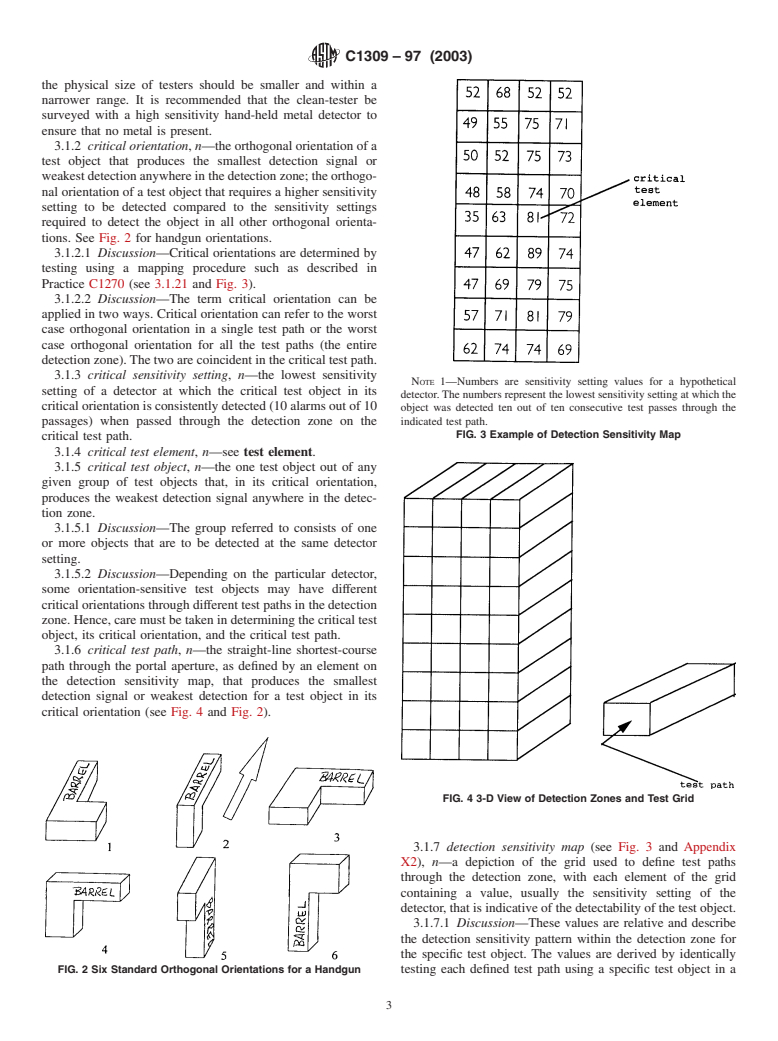
Questions, Comments and Discussion
Ask us and Technical Secretary will try to provide an answer. You can facilitate discussion about the standard in here.